This summer we created a self-learning firewall which secures all Hypernodes from security threats and constantly improves itself. After we’ve detected a certain pattern of attacks on Hypernode X, all Hypernodes on our platform are protected against this attack within the hour.
Time to end the cat-and-mouse game with spammers
In the past, each Hypernode only had a personal firewall consisting of manually updated blocklists and fail2ban. This was sufficient for a long time until some e-mail spammers found out that certain endpoints in Magento are easy to abuse. We already had static rules to block these kinds of spammers, but when crawling a large amount of Hypernodes at the same time a small amount of spam could still be sent out. Newsletter spam could occur by sending repeated requests to the newsletter subscription endpoint in Magento, including a personal message for the receiver, basically creating an open email relay form.
At the beginning of the summer, we noticed an increase of malicious crawling attempts to the newsletter subscription endpoint in Magento until they got blocked by fail2ban. This resulted in a cat-and-mouse game between our Tech department and the spammers. We kept tightening the fail2ban rules and they keep finding new holes. A new approach was needed.
Creating rules
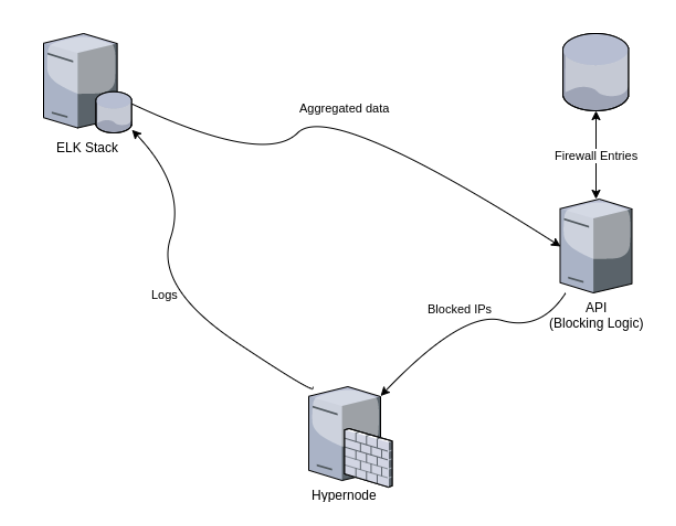
This brought us to the idea of a centralized firewall for all Hypernodes. Using aggregated Elasticsearch data we can look through the Hypernode logs and define suspicious browsing patterns. For example, if an IP POSTs to the newsletter endpoint more than a set number of times we flag this as a bad IP. When an IP is flagged as bad it gets added to the centralized firewall DB to be blocked for a certain amount of time. The block time is determined by the severity of the behaviour that was observed.
Blocking security threats with the Hypernode API
Now that we have a database of bad IPs we need to block these on the Hypernodes. Here comes our Hypernode API in play. We created a simple cronjob on all Hypernodes that talks to our API every hour requesting the current block list. If the list has been updated the script will update the local firewall and apply the changes.
A visualisation of the above looks like this:
Known and unknown security threats are immediately blocked on all Hypernodes
With this setup, we can identify and block new security threats within the hour. This process is fully automated. No human interaction is necessary, which makes it fast and safe.
The setup has been designed in such a way that we can extend it if more spammers or other types of abuse are discovered. This way our Tech department has the means to quickly react to emerging security threats.
So is it weird to say that at Hypernode you benefit from the security attack on somebody else’s store? Yeah, it’s weird. But it’s true 😉
Hi! My name is Dion, Account Manager at Hypernode
Want to know more about Hypernode's Managed E-commerce Hosting? Schedule your online meeting.
schedule one-on-one meeting +31 (0) 648362102