At Hypernode, we are committed to providing our customers with the best possible platform to develop, run and manage their applications. We understand that security is a top priority for our customers. Therefore, our goal is to ensure that our platform is secure and reliable. We recently discovered a new form of malware that affected a small number of our customers. This discovery was made after a customer alerted us that they had found evidence of the malware on their website. This malware was particularly sophisticated and used a new technique to hide both payload and communication from access logs and our Web Application Firewall. This made it much harder to detect, as it could blend in perfectly with legitimate requests.
Working closely with Sansec’s security experts, we were able to identify the source of the malware. From there, we were able to take steps to fix the problem for the affected customers. Interestingly, this particular strain was also new to Sansec, although they had seen similar malware infections. Our collaboration allowed them to improve their scanner and better protect other customers in the future.
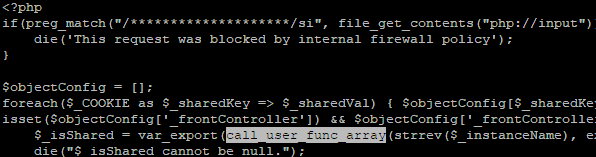
What was particularly interesting about this form of malware was that it contained a rudimentary firewall. This was designed to protect the application from the specific vulnerability that the attackers had exploited. This suggests that the attackers were aware of the possibility that other hackers would discover and exploit the vulnerability, and would take measures to protect themselves against it. By adding a firewall to prevent others from exploiting the same vulnerability, the attackers were able to maintain access to the affected websites even after the vulnerability was fixed.
After further investigation, we discovered that the attackers had gained access to the affected websites by exploiting a vulnerability in Magento 2. This vulnerability, known as CVE-2022-24086, had been patched earlier this year. Nevertheless, the affected customers had failed to (correctly) apply the patch, leaving their applications open to attacks. The attackers were able to exploit this vulnerability in order to gain access to the websites and insert the malware.
At Hypernode, we take the security of our platform and our customers’ applications very seriously, and we are committed to implementing the latest security measures and best practices to protect against potential threats. However, as always, it is also important for our customers to do their part in maintaining the security of their applications. We encourage all of our customers to regularly update their applications and stay current with the latest security patches in order to protect themselves against potential threats.
We are proud of the work we are doing to provide our customers with a secure and reliable platform. We will continue to work closely with security experts like Sansec, and implement the latest security measures and best practices, to ensure that our customers can focus on building great applications without worrying about security.
Speaking of security, also take a look at our service: magereport.com. Scan your Magento shop for known vulnerabilities. Get insight into the security status of your Magento shop(s) and learn how to fix potential vulnerabilities, for free!
If you have any questions about this article, feel free to contact us. We are happy to help you.
Hi! My name is Dion, Account Manager at Hypernode
Want to know more about Hypernode's Managed E-commerce Hosting? Schedule your online meeting.
schedule one-on-one meeting +31 (0) 648362102